During the past few weeks, I have described what a secrets manager is and I have given an overview of the architecture and system requirements of CyberArk Conjur.
A secrets manager can't do his job if he can't talk to those who need to ask him for secrets, and that's where Conjur's magic comes in!
The "authenticators" are responsible of the authentication process in Conjur and they are specialised to make it in the most secure way depending on the service.
Here is the list of the authenticators currently supported :| authn | Defines the Conjur default authenticator. Authentication for both users and hosts is based on an ID and API key. |
| authn-oidc | Leverages the identity layer provided by OIDC to allow applications to authenticate with Conjur and retrieve secrets needed for connecting to services such as a database. |
| authn-iam | Enables an AWS resource to use its AWS IAM role to authenticate with Conjur. |
Enables an Azure resource to authenticate with Conjur | |
Enables an application to authenticate to Conjur using a JWT from a JWT Provider. | |
Enables a Google Cloud Platform resource to authenticate with Conjur | |
| authn-k8s | Authenticates hosts that are Kubernetes resources, such as a Kubernetes namespace, deployment, stateful set, and others. Authentication is certificate-based using a mutual TLS connection. |
| authn-ldap | Authenticates users based on an LDAP directory. |
By default, after the initial setup, authn is the only authenticator enabled and it's responsible of the Conjur access with username or API key (randomly generated between 51 and 56 characters).
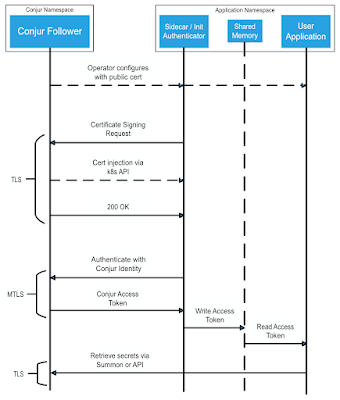
When integrations are needed, for example with a Kubernetes cluster, you need to activate and configurate the authn-k8s authenticator.
This authenticator can establish a secure mTLS connection compliant with Spiffie framework, as described in the following diagram (click here for more details):
If you need integrations with cloud identities supporting JWT authentications, like Google Apigee, you will enable the authn-jwt authenticator that will perform the integrations as below:
- Kubernetes (locali o cloud)
- API gateway
- Jenkins
- Ansible
- Puppet
- Terraform
- Cloud services
If the scenario described sound interesting for your needs, Conjur can definitely be the right choice, so contact your sales representative at CyberArk or your preferred CyberArk business partner..


No comments:
Post a Comment